Sonatus Foundation
Deliver a future-ready vehicle platform
Build a vehicle E/E architecture with a flexible foundation to support evolving customer and market needs
Drive continuous vehicle improvements with a software-defined architecture
Sonatus Foundation provides essential software building blocks that add flexibility, configurability, and upgradeability to vehicle Electronic/Electronic (E/E) architectures.
Accelerate
time-to-market
Adopt a market-ready and modular product designed to adapt to your specific E/E design, creating a vehicle architecture that allows designers to focus on differentiating features and applications.
Enable continuous enhancements
Add dynamic configurability to your vehicle E/E architecture to continuously adapt to changes in vehicle electronics, security demands, application workloads, and user experiences.
Future-proof
vehicle architectures
Build vehicle platforms with technologies that meet current and upcoming infrastructure requirements, including zonal and centralized high-performance compute architectures.
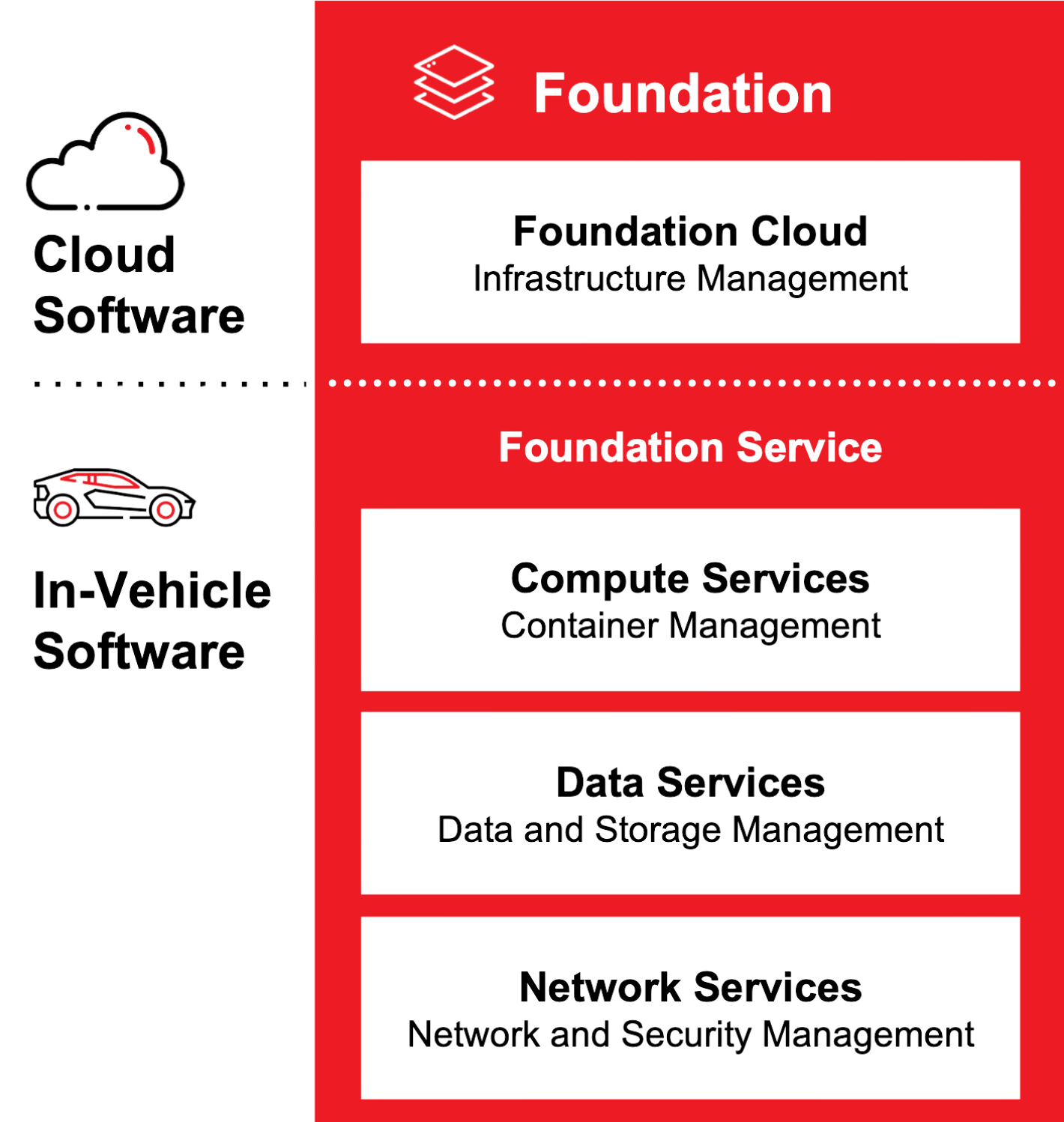
Features
Sonatus Foundation includes several major software technology building blocks to help accelerate the transition to a dynamic and adaptable hardware architecture for vehicles of all types.
Network Services
Dynamically manage and adapt vehicle networks to accommodate mixed-criticality application workloads with varying requirements for bandwidth, latency, security, and resilience.
- In-Vehicle Network Manager
- Hardware-agnostic switch interface abstraction
- Real-time control, adaptive configuration, OTA-ready
- High-performance, SDV-ready network foundation
- Deep network diagnostics and visibility
- Reliable and safe network OTA updates
- End-to-end automotive network security
Data Services
Evolve from a signal-based to a service-oriented data exchange to enable cross-domain applications and streamline in-vehicle data storage and access.
- Service-Oriented Architecture (SOA) Adapter
- Configuration Management
- Multi-protocol support
- Dynamic service integration
- Real-time service discovery
- Robust security and access control
- Scalable and high-performance
- Network shared storage
- Adaptive, usage-based storage management
- Virtualized, compressed, and purge-ready storage
- Secure data access with encryption controls
- Cloud-synced policies and health monitoring
Compute Services
Simplify the creation, deployment, configuration, and management of containerized automotive applications to support cloud-native application development and deployment.
- Container Manager
- Container lifecycle management
- Compatible with POSIX OS, Adaptive AUTOSAR, SOA
- Fine-grained resource isolation and access control
- Virtual network for container-to-container and host communication
- Runtime isolation of containers for security
- OTA updates of container images